Build with



Get started with Parallel’s web APIs - including the Task API, Search API and Chat API.
.svg)
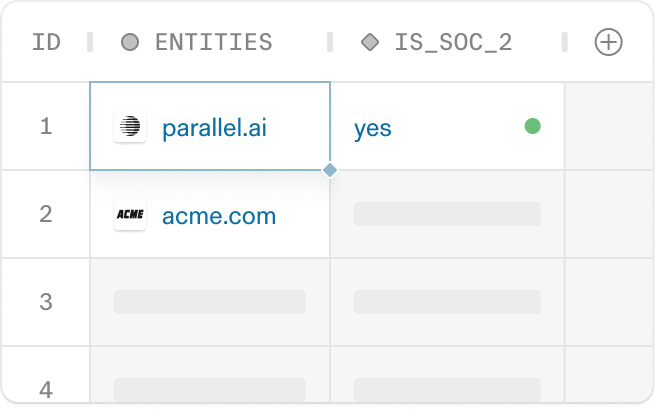
Task API Quickstart
Enrich a list of entities, optimized for quality & freshness
5s - 30min, async$0.005 - $2.42,000 requests / min
.svg)
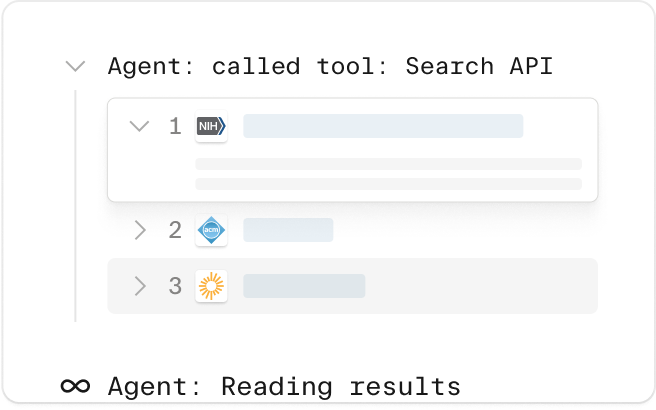
Search API Quickstart
Ranked web URLs with long, relevant content
< 3s, sync$0.004 - $0.009600 requests / min
.svg)
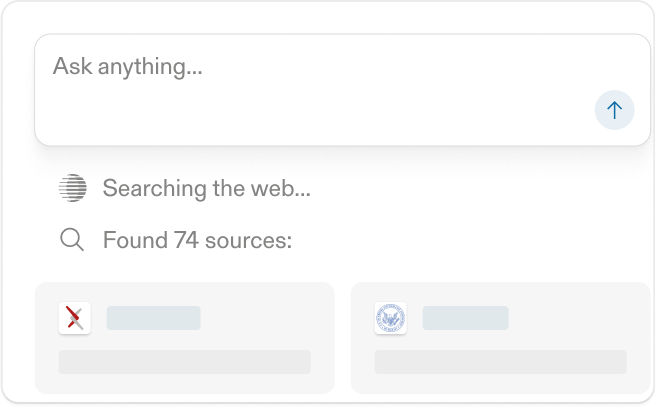
Chat API Quickstart
Fast, web-researched LLM completions
< 5s, sync$0.00530 requests / min
Resources
Remote MCP
Use our Search API via a remote MCP Server for easy integration.
Python SDK
Get started with our Python SDK for seamless integration into your applications
Pricing Guide
Recipes and apps for real-world use cases optimized for LLM context
API Reference
Complete API documentation for all generally available APIs
Output Basis
Learn about citations, reasoning, and how Parallel ensures high-quality research outputs
Processors Overview
Compare different processing options and choose the right one for your use case

